What is X.509 Certificate?
- X.509 certificates are digital documents that are used to verify the identity of individuals, organizations, or devices over the internet. They are widely used in various applications like secure email, web browsing, online banking, and electronic transactions.?An X.509 certificate contains information about the certificate holder's identity, such as their name, public key, digital signature, and the name of the certificate authority (CA) that issued the certificate.The public key is used to encrypt messages, and the digital signature is used to verify that the message was sent by the holder of the private key associated with the public key.In other words, an X.509 certificate acts like a digital identity card that enables secure communication and transaction between two parties. The use of X.509 certificates ensures that the communication is encrypted and authenticated, thereby providing a high level of security for online transactions.
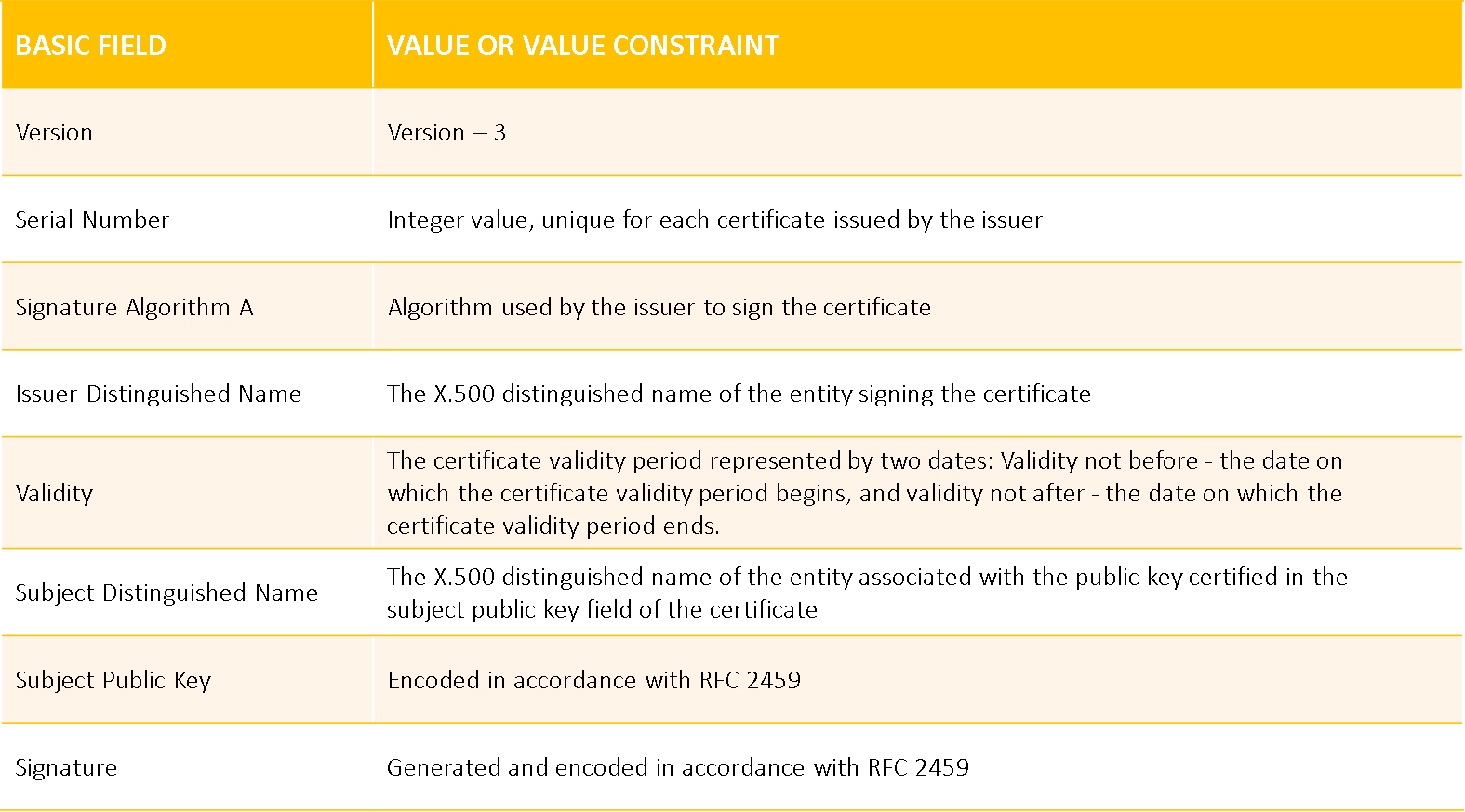
X.509 Digital Certificate Profile
What is X.509 Certificates used for?
X.509 certificates are used for various purposes related to secure communication and digital identity verification. Some of the most common uses of X.509 certificates include:
- SSL/TLS Encryption: X.509 certificates establish secure communication between a web browser and a web server. When you visit a website with "https" in the URL, the website uses SSL/TLS encryption, and X.509 certificates are used to authenticate the website and encrypt the communication between the browser and the server.
- Code Signing: X.509 certificates are used to digitally sign software code, ensuring that the code is from a trusted source and has not been tampered with.
- Email Security: X.509 certificates are used to provide secure email communication by encrypting email messages and verifying the identity of the sender.
- VPN Authentication: X.509 certificates are used to authenticate users in virtual private network (VPN) connections.
- Document Signing: X.509 certificates are used to sign electronic documents, providing assurance that the document is from a trusted source and has not been modified since it was signed.
- User Authentication: X.509 certificates are used to authenticate users in various applications, including online banking, e-commerce, and other online services.In summary, X.509 certificates are essential for ensuring secure communication and verifying digital identities across various applications and services.
What does an X.509 Certificate contain?
An X.509 certificate contains several pieces of information, including:
- Version Number: The version number of the X.509 certificate.
- Serial Number: A unique identifier assigned to the certificate by the issuer.
- Signature Algorithm: The algorithm used to create the digital signature.
- Issuer: The name of the organization or entity that issued the certificate.
- Validity Period: The period during which the certificate is valid, including the start and end dates.
- Subject: The name of the certificate holder or entity.
- Public Key: The public key associated with the certificate holder.
- Extensions: Additional information included in the certificate, such as the intended usage of the certificate, the certificate revocation list (CRL), or other custom data.
- Digital Signature: The digital signature created by the issuer to verify the authenticity of the certificate.An X.509 certificate is a digital document that contains essential information about the certificate holder's identity, public key, and digital signature, enabling secure communication and digital identity verification.
What are the benefits of X.509 Certificates?
There are several benefits of using X.509 certificates:
- Secure communication: X.509 certificates enable secure communication between two parties, ensuring that the communication is encrypted and authenticated, and preventing unauthorized access or interception of data.
- Digital identity verification: X.509 certificates provide a secure and reliable way to verify the digital identity of individuals, organizations, or devices, ensuring that the data or transaction is from a trusted source.
- Interoperability: X.509 certificates are widely used and recognized by various applications and platforms, providing interoperability across different systems and ensuring that the certificate can be used in different environments.
- Scalability: X.509 certificates can be easily scaled to support large-scale deployments, enabling organizations to manage and authenticate a large number of users or devices securely.
- Compliance: X.509 certificates are often required by industry standards and regulations, ensuring that organizations comply with security and privacy requirements.
- Flexibility: X.509 certificates can be customized to include additional information or extensions, enabling organizations to add specific requirements or information as needed.
Overall, X.509 certificates provide a secure and reliable way to establish trust and ensure secure communication and digital identity verification in various applications and industries.
How does an X.509 Certificate work?
An X.509 certificate works through a process called public-key cryptography. Here are the basic steps of how an X.509 certificate works:
- Certificate Request: The certificate holder generates a public-private key pair and submits a certificate request to a trusted certificate authority (CA).
- Verification: The CA verifies the identity of the certificate holder and validates the certificate request.
- Certificate Issuance: The CA issues an X.509 certificate containing the certificate holder's public key and other identifying information, digitally signed by the CA's private key.
- Certificate Distribution: The CA distributes the X.509 certificate to the certificate holder and other relevant parties as necessary.
- Certificate Verification: When the certificate holder attempts to establish a secure communication or transaction, the recipient verifies the certificate's authenticity by checking the digital signature of the CA and the validity period of the certificate.
- Key Exchange: Once the certificate is verified, the recipient encrypts a session key using the certificate holder's public key and sends it back to the certificate holder.
- Secure Communication: The certificate holder uses their private key to decrypt the session key and establishes a secure communication session using the session key.
An X.509 certificate provides a secure and trusted way to verify the identity of individuals or entities and establish secure communication or transactions using public-key cryptography. The X.509 certificate contains the public key of the certificate holder and other identifying information, digitally signed by a trusted CA. It is used to verify the authenticity of the certificate holder and establish secure communication.
What is the role of X.509 Certificates in Cryptography?
X.509 certificates play a critical role in cryptography, particularly in public-key cryptography. Here are some of the key roles of X.509 certificates in cryptography:
- Digital Identity Verification: X.509 certificates provide a secure and trusted way to verify the digital identity of individuals, organizations, or devices, ensuring that the data or transaction is from a trusted source.
- Key Distribution: X.509 certificates enable the secure distribution of public keys, ensuring that the public key of the certificate holder is authentic and has not been tampered with.
- Digital Signature: X.509 certificates are used to create and verify digital signatures, ensuring that the data or transaction is authentic and has not been modified since it was signed.
- Secure Communication: X.509 certificates enable secure communication through the use of public-key cryptography, ensuring that the communication is encrypted and authenticated, and preventing unauthorized access or interception of data.
- Certificate Management: X.509 certificates provide a standardized way to manage digital certificates, including issuance, revocation, and renewal, ensuring that the certificates are up-to-date and valid.
Overall, X.509 certificates play a crucial role in providing secure communication, digital identity verification, and digital signature validation in cryptography. They are widely used in various applications and industries to ensure secure and reliable communication and transactions.
How do I get an x.509 Certificate?
To get an X.509 certificate, you need to follow these steps:
- Generate a public-private key pair: You need to generate a public-private key pair using a cryptographic algorithm such as RSA or ECC. This key pair will be used to create and verify digital signatures and encrypt and decrypt data.
- Create a certificate request: Once you have generated a key pair, you need to create a certificate request that contains information about the key pair and the identity of the certificate holder.
- Submit the certificate request: You must submit the certificate request to a trusted Certificate Authority (CA) that can verify your identity and issue a valid X.509 certificate. You can choose a public CA like Let's Encrypt, or a private CA for your organization.
- Verify your identity: The CA will verify your identity and validate the certificate request, typically by sending an email or performing other forms of identity verification.
- Receive the X.509 Certificate: Once the CA has validated your identity and the certificate request, they will issue an X.509 certificate that contains your public key, identity information, and other metadata, digitally signed by the CA's private key.
- Install the certificate: Finally, you need to install the X.509 certificate on your server or device, typically by importing the certificate file into the appropriate certificate store or configuration file.
The process of getting an X.509 certificate involves generating a key pair, creating a certificate request, submitting the request to a trusted CA, verifying your identity, receiving the X.509 certificate, and installing it on your server or device. The process may vary depending on the CA and the specific application or use case.

